Elevate your existing TPRM program
Mirato’s TPRM intelligence platform leverages AI, and Natural Language Processing (NLP) to collect, analyze and correlate the data from questionnaires, evidence documents, and external sources. It validates your controls for you, enabling your organization to achieve:
Explore some of our features:
Mirato understands and correlates structured and unstructured data using a highly innovative approach based on methodologies used by intelligence agencies. The Mirato engine reads and interprets the meaning within your questionnaires, documents and data feeds to cross-validate and augment every data point and generate contextual insights.
Mirato’s unique ability enables you to unearth issues that otherwise would remain hidden. This allows you to truly leverage the value of multiple data sources and identify risk within your third-parties, ranging from insufficient controls to fourth parties, locations, online asset information, and more.
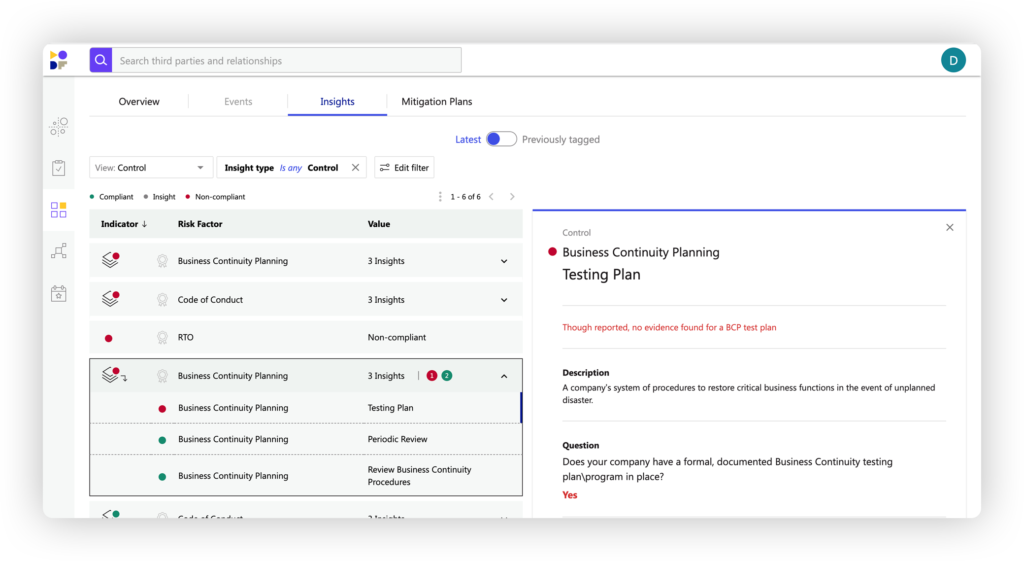
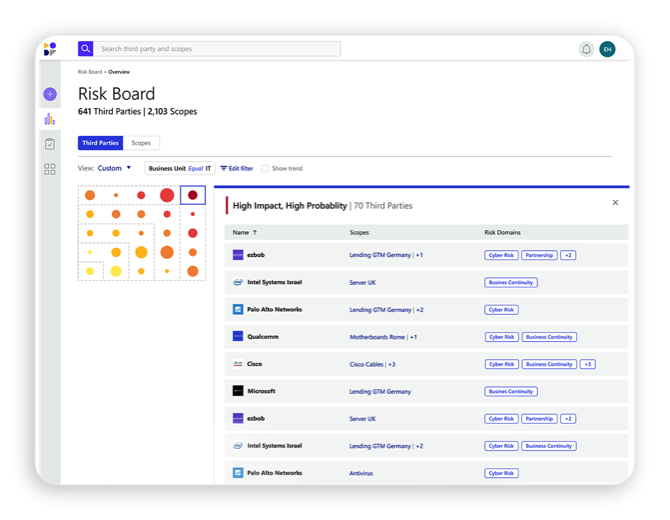
Get an overview of your third-party state of risk. Easily see how vendors and relationships affect your risk. View trends across time, risk domains or business units, or even all of them together. Zoom in on each specific third party to instantly get all the bottom-line information you need to decide your next steps.
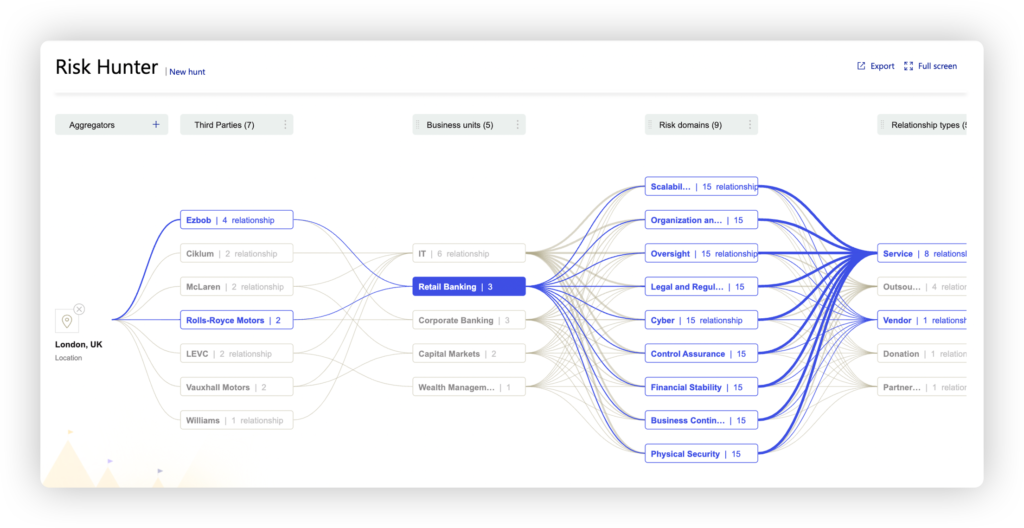
Fully understanding all the cascading effects of a negative incident is extremely difficult. Mirato’s Risk Hunter automatically creates a map that clearly displays how a single point of failure impacts your organization, including the third and fourth parties affected, which engagements and business units are involved, even the relationship manager that own the relationship. Our powerful analytics engine can correlate and understand multiple types of concentration points such as 4th parties, people, locations, open-source packages, vulnerabilities and many more.
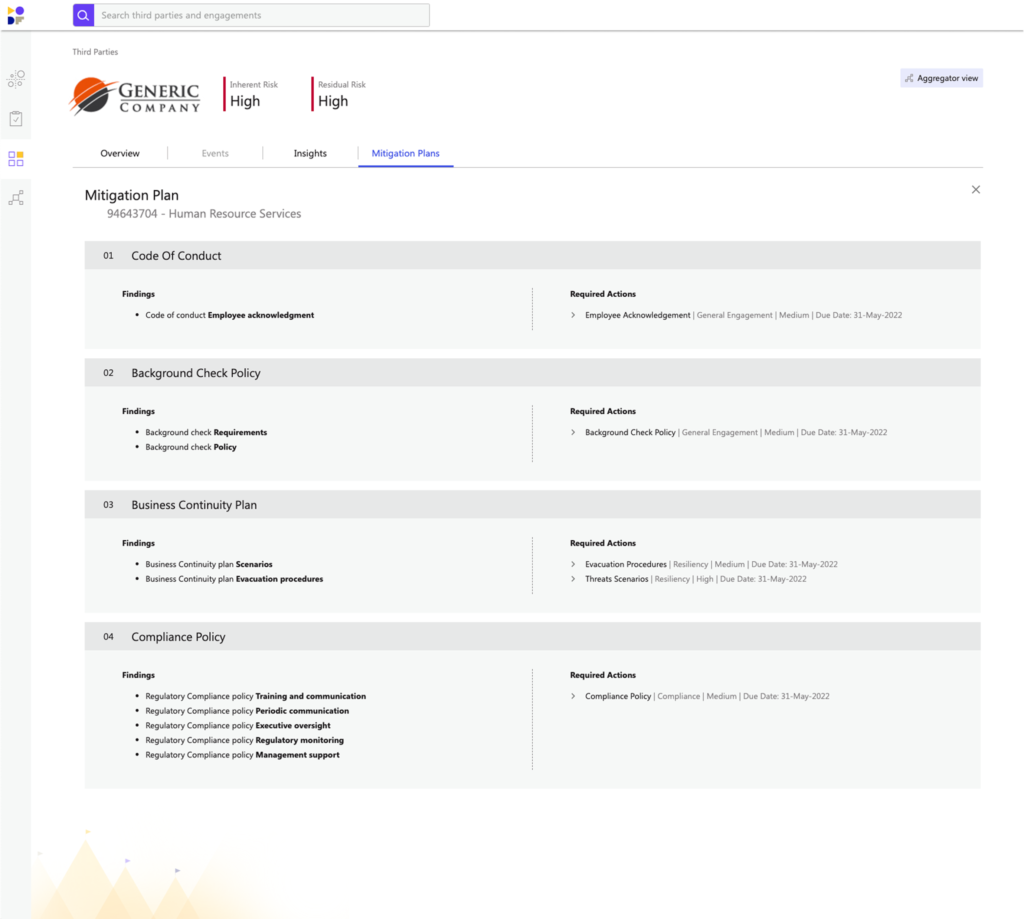
Mirato’s AI-powered insights generate automated mitigation plans to address issues and deficiencies found during due diligence, periodic reviews, ongoing monitoring, and desktop or on-site control assessments.
This reduces the manual effort and tedious nature of current approaches while improving the quality and consistency of this work product. Mirato mitigation plans are driven by your unique TPRM program, risk appetite, and framework requirements, and include details of all deficiencies, roles, responsibilities, steps, timing, requirements, etc., required to remediate the identified shortcomings.
You can easily view Mirato mitigation plans on-screen, instantly convert them into your company branded and formatted PowerPoint for easier and more effective communication between the relationship manager and the third party, and/or output them to your issue management system to trigger external workflow and progress if desired.